Every year, cyber-attacks and threats become more widespread and complex. Individuals, corporations, and governments must be aware of these dangers and take actions to protect themselves now more than ever. Cyber-attacks can result in financial loss, data loss, and even death.
Malware
Computer malware is a type of software that is created with the intent of harming or disabling computers. Viruses, ransomware, and spyware are examples of malware that can be installed mistakenly or maliciously. Malware has the ability to corrupt files, slow down computer performance, and steal data. It can also allow hackers to remotely access and control computer systems.
Phishing
Phishing is a sort of cyberattack in which an attacker impersonates a trustworthy entity in an electronic conversation in order to get sensitive information such as usernames, passwords, and credit card numbers. Phishing is most commonly done by email, however it can also be done via text messaging and social media platforms.
Person-in-the-Middle
A person-in-the-middle (PitM or MitM) attack is a type of computer security attack in which the attacker places themselves between two communicating parties in order to read, manipulate, or disrupt the conversation. This can be done for a variety of purposes, including monetary gain, espionage, or simply to cause mischief. In some circumstances, the attacker may even impersonate one of the communication parties to obtain access to information that they would not otherwise have access to.
Zero-Day Exploit
Zero-day exploits are security vulnerabilities that are unknown to the public and the vendor. These vulnerabilities are typically discovered by security researchers and are not fixed until a security patch is released. Because zero-day exploits are unknown, they can be used to attack systems without being detected.
Denial-of-Service Attack
A denial-of-service (DoS) attack is an attempt to make a machine or network resource unavailable to its intended users. Attackers can use a number of methods to achieve this, such as flooding the target machine with requests so that it can't respond to legitimate traffic.
SQL Injection
A SQL injection vulnerability is a security hole that allows an attacker to inject malicious SQL code into an SQL statement, potentially resulting in the execution of the code by the database. This can allow the attacker to access and manipulate data, steal information, or even take complete control of the database. SQL injection vulnerabilities are a common security vulnerability, and are often exploited by attackers.
Web Shell
A web shell is a script that can be uploaded to a web server to provide an attacker with a remote command line interface. This can be used to execute commands on the server and to access the file system. Web shells are often used to upload and run malicious code, or to steal sensitive information. They can also be used to take control of the server and to launch a denial of service attack.
Malicious Insider
A malicious insider is an employee who intentionally harms their organization. They may steal or leak confidential information, sabotages systems, or even commit fraud. Malicious insiders can cause a great deal of damage, and are a serious threat to businesses.
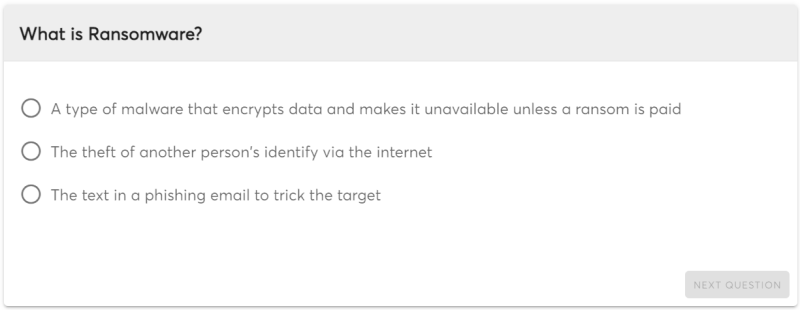
Ransomware
Ransomware is a type of malware that locks users out of their devices or encrypts their files and demands a ransom payment to unlock them. The ransomware can be delivered through a variety of means, including phishing emails, infected websites, or trojan horses. Once installed, the ransomware will typically display a message informing the user that their device has been locked or their files have been encrypted and demanding a ransom payment to unlock them.
Data Spill
A data spill is an inadvertent release of confidential or sensitive information. This can include, but is not limited to, the release of Personally Identifiable Information (PII), Protected Health Information (PHI), or credit card numbers. Data spills can occur in a number of ways, including but not limited to: emailing the wrong person, leaving documents in a public place, or uploading files to the wrong server. The consequences of a data spill can be significant, including fines, loss of customers, and damage to reputation. Data spills should be taken seriously and steps should be taken to prevent them from occurring.
Identity Theft
A crime in which someone acquires key pieces of personal information such as name, Social Security number, or credit card number, in order to impersonate another person. Identity theft can be committed in a variety of ways, including stealing mail, hacking into computer systems, or stealing personal information from the victim. The goal of identity theft is usually to gain access to the victim's finances or to obtain government benefits in the victim's name.
Advanced Persistent Threat
An Advanced Persistent Threat (APT) is a cyberattack that is carried out over a long period of time and is meant to achieve a specific goal, such as stealing confidential data. APTs are often conducted by state-sponsored actors or criminal organizations and can be very difficult to detect.

 Beginner
Beginner