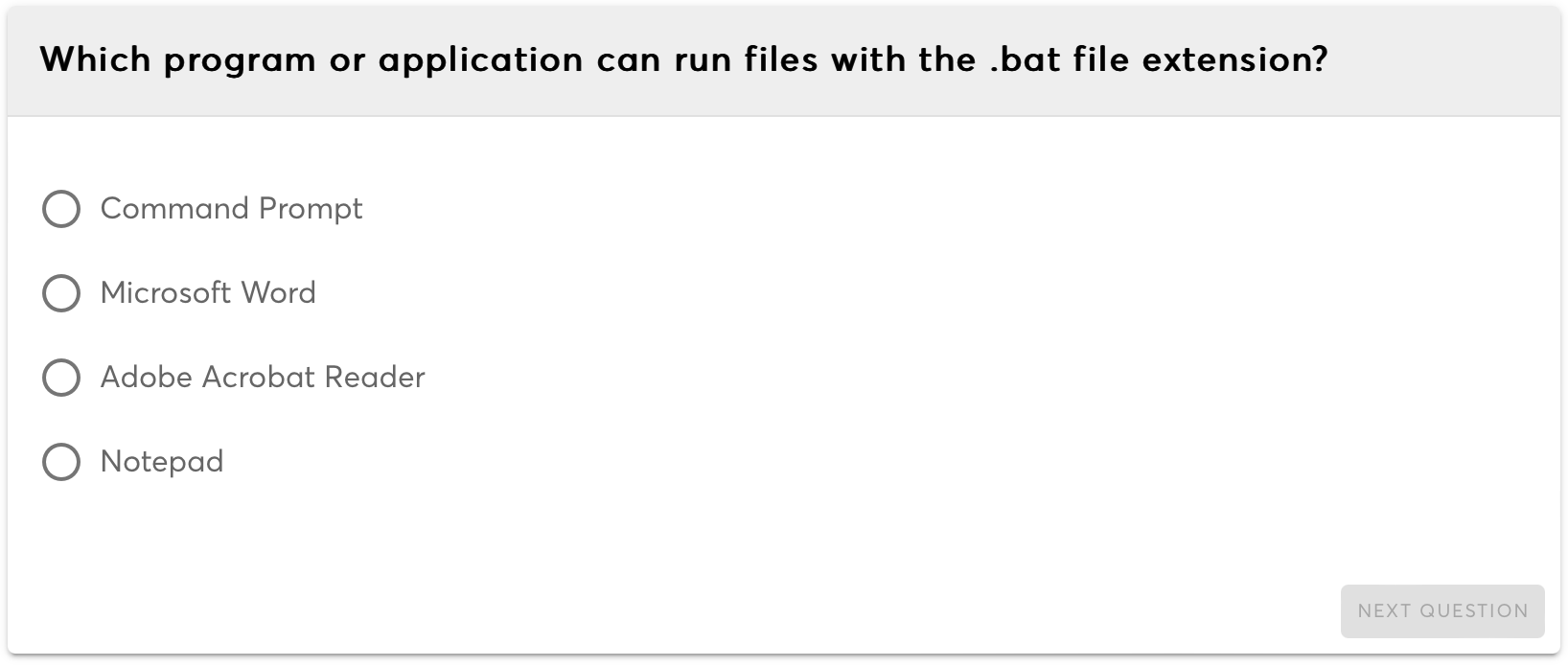
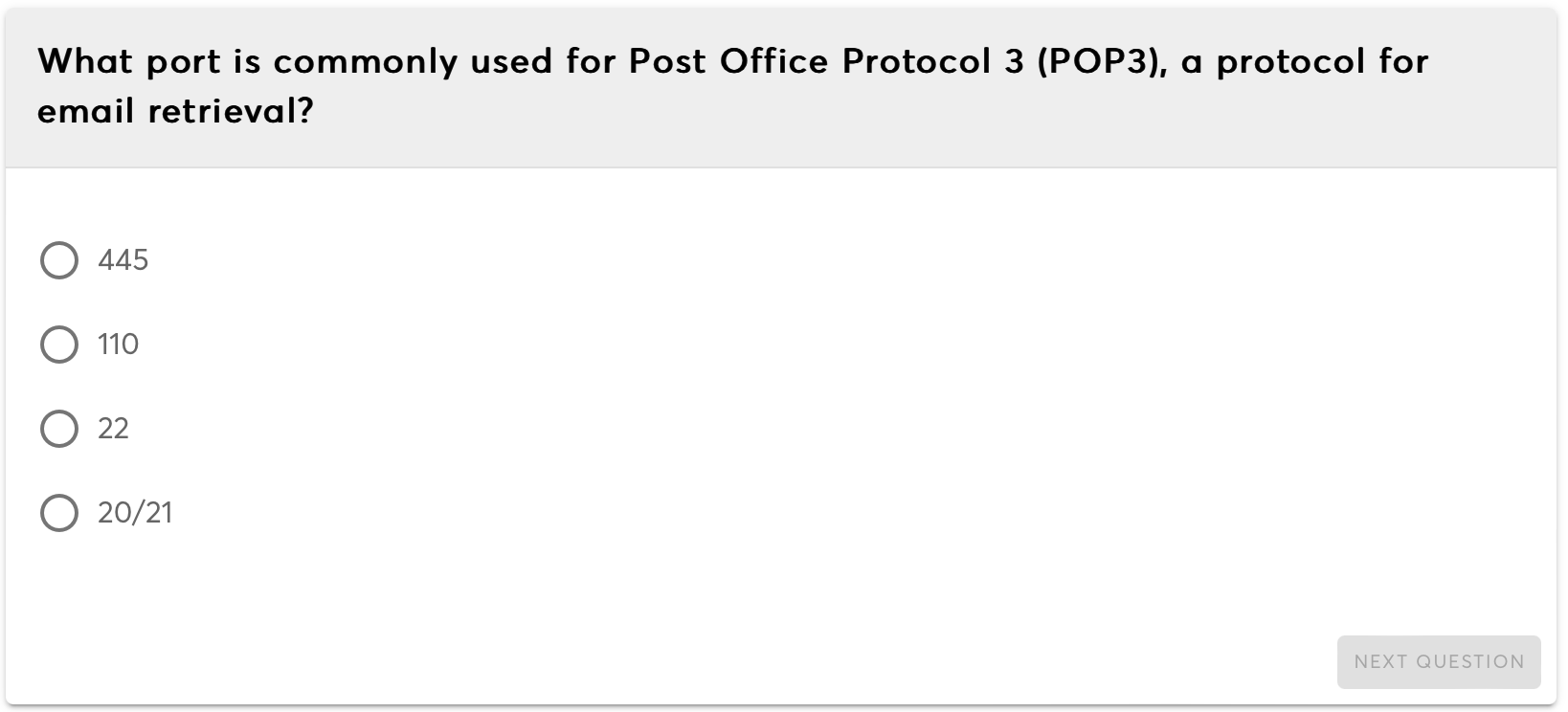
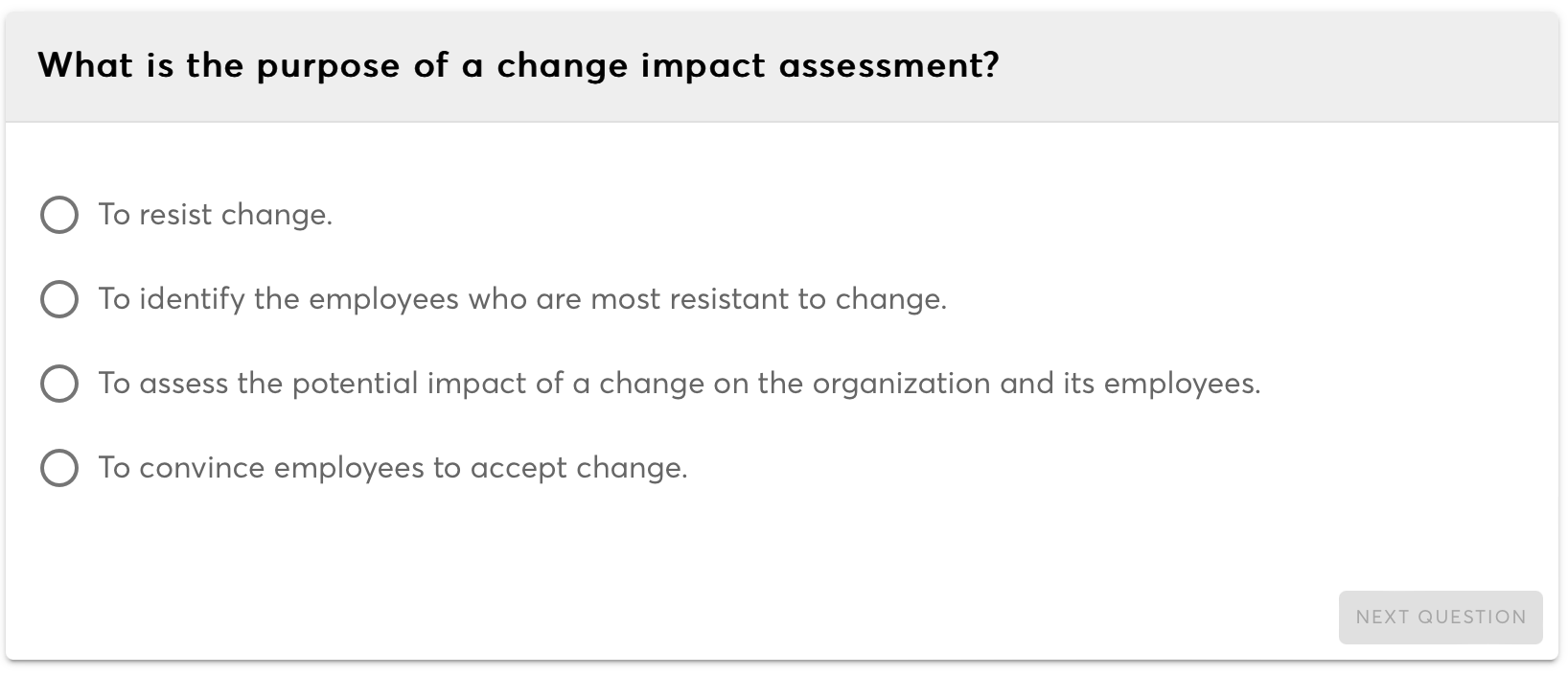
Security is paramount in IT systems, encompassing strategies, technologies, and practices to protect data, systems, and networks from unauthorized access, attacks, and vulnerabilities.
Active Directory
Active Directory is a Microsoft directory service that manages user accounts, computers, groups, and permissions within a network domain, providing centralized authentication and access control.
Physical Security
Physical security involves securing physical assets and infrastructure (e.g., buildings, servers) from unauthorized access, theft, or damage. An example of physical security is using access control systems like keycards or biometric scanners to restrict entry to a data center.
Kerberos
Kerberos is a network authentication protocol used to verify the identity of users and services over a non-secure network, providing mutual authentication and encryption to prevent eavesdropping and spoofing attacks.
Advanced Encryption Standard (AES)
AES is a symmetric encryption algorithm widely used to secure sensitive data, such as in secure communications (e.g., HTTPS) and encrypted storage (e.g., BitLocker).
Trojan
A Trojan is a type of malware disguised as legitimate software that tricks users into executing malicious actions, such as stealing sensitive information or providing remote access to attackers.
Spyware
Spyware is a form of malware designed to secretly monitor user activities, gather personal information, and transmit data to unauthorized parties without the user's consent.
Cryptominers
Cryptominers are malicious software that hijacks computer resources to mine cryptocurrencies without the user's permission, leading to system slowdowns and increased energy consumption.
Anti-phishing Training
Anti-phishing training educates users about phishing threats and techniques to recognize and avoid phishing attacks, reducing the risk of data breaches and unauthorized access.
Antivirus
Antivirus software detects, prevents, and removes malicious software (malware) from computer systems, providing essential protection against viruses, worms, trojans, and other threats.
Social Engineering
Social engineering is a tactic used by attackers to manipulate individuals into divulging confidential information or performing actions that compromise security. An example of social engineering is a phishing email that tricks users into clicking on malicious links or providing login credentials.
Tailgating
Tailgating is a physical security breach where unauthorized individuals gain access to a secured area by closely following authorized personnel through a secure entry point.
Shoulder Surfing
Shoulder surfing is the practice of spying on sensitive information (e.g., passwords, PINs) by observing someone's computer screen or keypad from a nearby location.
Brute-force Attack
A brute-force attack is a trial-and-error method used by attackers to crack passwords or encryption keys by systematically checking all possible combinations until the correct one is found.
Dictionary Attack
A dictionary attack is a type of brute-force attack that uses a predefined list of words (dictionary) to attempt to guess passwords or encryption keys.
User Account Control (UAC)
User Account Control (UAC) is a security feature in Windows that helps prevent unauthorized changes to the system by requiring users to confirm administrative actions with a prompt or password.
Disabling AutoRun
Disabling AutoRun is important to prevent the automatic execution of malicious software from removable media (e.g., USB drives) when inserted into a computer, reducing the risk of malware infections.
Screensaver Locks
Screensaver locks automatically lock the screen after a period of inactivity, requiring users to enter a password to regain access, thereby preventing unauthorized access to the system.
Degaussing
Degaussing is the process of erasing data from magnetic media (e.g., hard drives, tapes) by demagnetizing the surface, rendering the data irretrievable and ensuring secure data disposal.
IP Filtering
IP filtering is a security measure that controls access to networks or resources based on source or destination IP addresses, allowing or blocking specific traffic based on predefined rules.
Port Forwarding/Mapping
Port forwarding or mapping is a technique used to redirect incoming network traffic from one port to another, enabling remote access to specific services or applications hosted on internal network devices.
Universal Plug and Play (UPnP)
Universal Plug and Play (UPnP) is a set of networking protocols that enable devices to discover each other on a network, automatically establish connections, and simplify the configuration of networked devices.
Default Passwords
Changing default passwords is important to prevent unauthorized access to devices or systems, as default passwords are often well-known and susceptible to exploitation by attackers.
Ad Blocker
An ad blocker is a software tool that prevents advertisements from displaying on web browsers, reducing exposure to potentially malicious or unwanted content while improving browsing speed and privacy.

 Beginner
Beginner