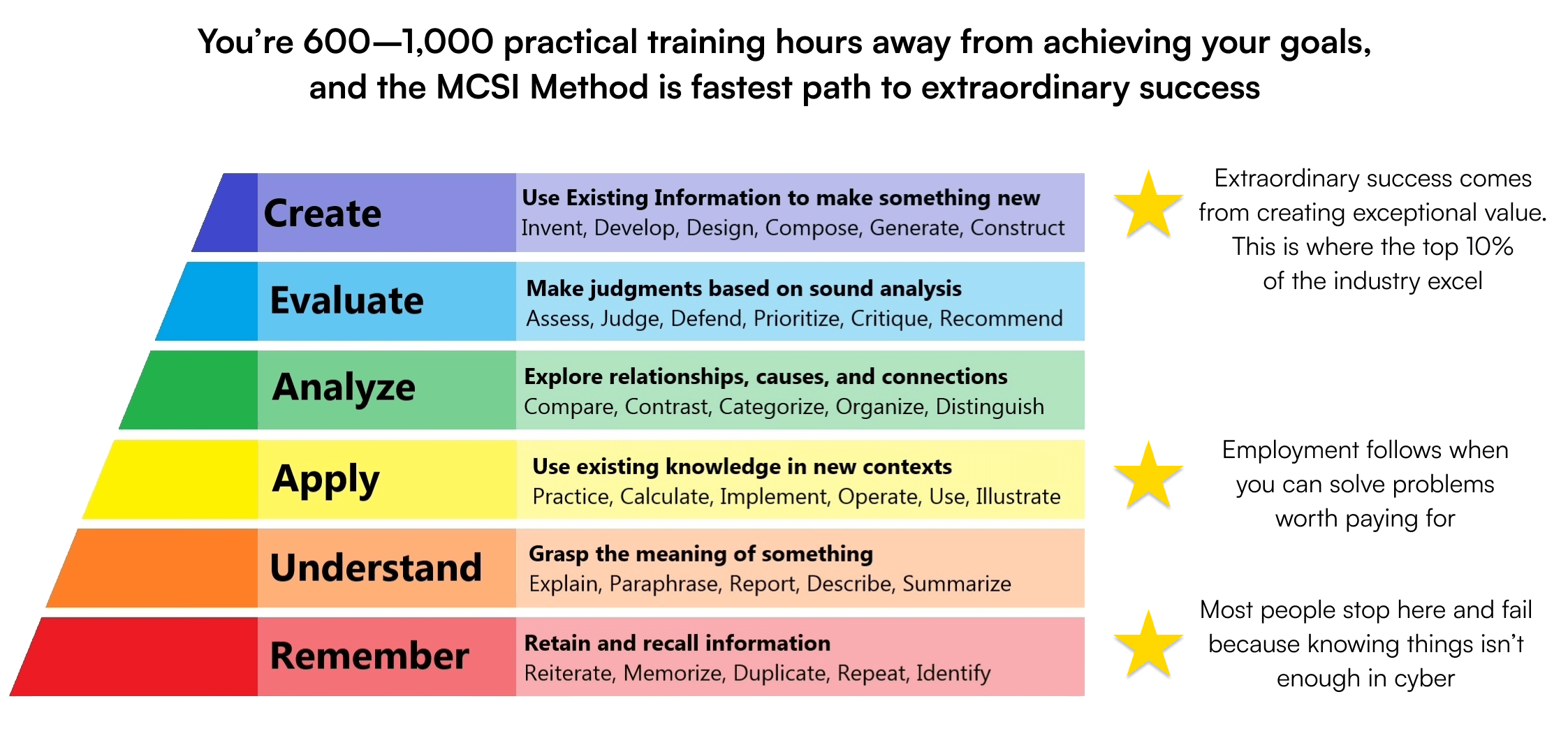
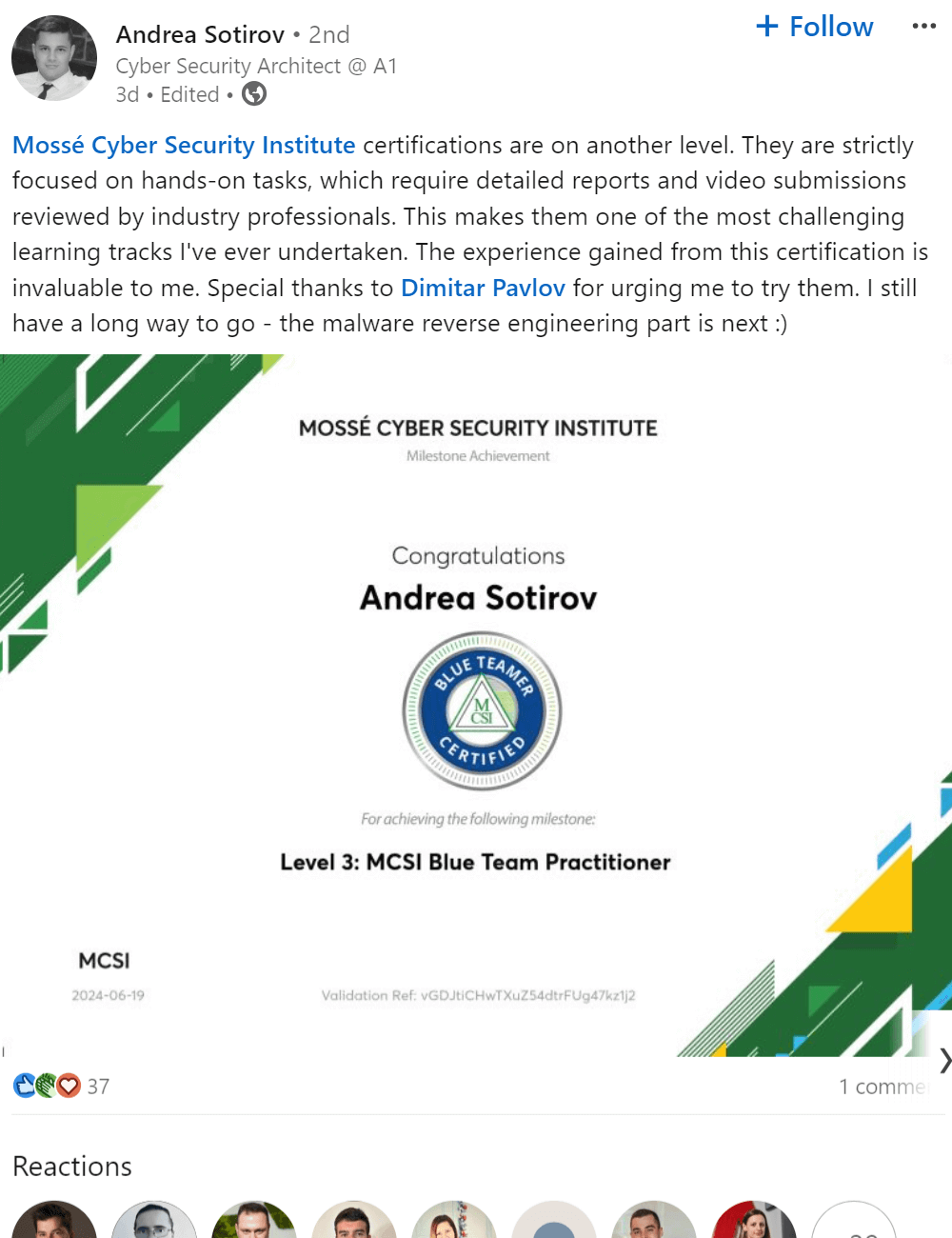
MCSI certifications are highly respected, showcasing your expertise and commitment to excellence. With cutting-edge, hands-on content, our exercises teach in-demand skills for immediate application. Certifications are valid for life, with no renewal fees or time limits.
Syllabus
Training Modules
This course provides you with multiple training modules, each of which is designed to teach you practical skills that can help you solve important cyber problems. Each module offers exercises that will help you build your skills and capabilities.
-
MRE-QS-001:
Quickstarter
- 9 exercises
-
MRE-001:
Lab Setup
- 4 exercises
-
MRE-002:
Fundamentals, Concepts, and Theory
- 4 exercises
-
MRE-003:
Programming for Reverse Engineering
- 5 exercises
-
MRE-004:
Windows Internals for Reverse Engineering
- 6 exercises
-
MRE-101:
Binary Classification
- 8 exercises
-
MRE-102:
Behavioral Analysis
- 5 exercises
-
MRE-103:
Memory Forensics for Malware Analysis
- 3 exercises
-
MRE-104:
Ghidra
- 8 exercises
-
MRE-105:
Malware in Documents
- 2 exercises
-
MRE-201:
Static Code Analysis
- 9 exercises
-
MRE-202:
Dynamic Code Analysis
- 7 exercises
-
MRE-301:
Manual Decompilation
- 4 exercises
-
MRE-302:
Code Deobfuscation
- 10 exercises
-
MRE-303:
Advanced Memory Forensics
- 3 exercises
Scenarios
Cyber professionals must be ready for everything. The typical security training strategy, which focuses on individual skills and tools, is insufficient. You must be able to operate as part of a team, see the big picture, and respond swiftly and effectively to unforeseen circumstances. That's why, as part of our training, we use replays of whole cyber missions. Our scenarios help you prepare for the demands of the job and give you confidence in your ability to work professionally.
-
MRE-SC-01:
Systematic Code Analysis
- 4 exercises
-
MRE-SC-02:
Systematic Approach to Malware Analysis
- 5 exercises
⚡
Enroll now with lifetime access for
$699
→
Certifications
MCSI Industry Certifications are important for you to earn because they signify that you have the skills required to work in a cybersecurity. Certificates of Completion are also important to earn because they signify that you have completed an exercise. Earning Certificates of Completion and Industry Certifications demonstrates that you are willing to put in the extra work to be successful.
1

Learn in-demand practical skills
2

Receive tailored feedback
3

Earn 5 certificates & build a portfolio
4

Unlock career opportunities
MCSI's MRE certification provides you with the required skills and knowledge aligned to the Australian Signals Directorate's
Cyber Skills Framework
. Upon reaching each level, you will earn a certificate of achievement.
Click here to learn more about our multi-credentialed approach.
|
|
Certificate Level
|
Curriculum Completion Requirement
|
Scenarios Completion Requirement
|
|
MCSI Reverse Engineering Learner
|
Level 1
|
0%
|
0%
|
|
MCSI Novice Reverse Engineer
|
Level 2
|
20%
|
0%
|
|
MCSI Reverse Engineering Practitioner
|
Level 3
|
50%
|
10%
|
|
MCSI Senior Reverse Engineering Practitioner
|
Level 4
|
70%
|
30%
|
|
MCSI Certified Principal Reverse Engineer Practitioner
|
Level 5
|
80%
|
50%
|
|
MCSI Certified Expert Reverse Engineering Practitioner
|
Level 6
|
95%
|
75%
|
In a single course, MCSI offers multiple industry certifications. You will save time and money with us because you will receive several accredited levels of competencies with a single purchase rather than having to buy multiple courses. Our goal is to provide you with a course that will take you from beginner to expert.
Sample Exercises
Decompile A Malicious Java Executable (Novice)
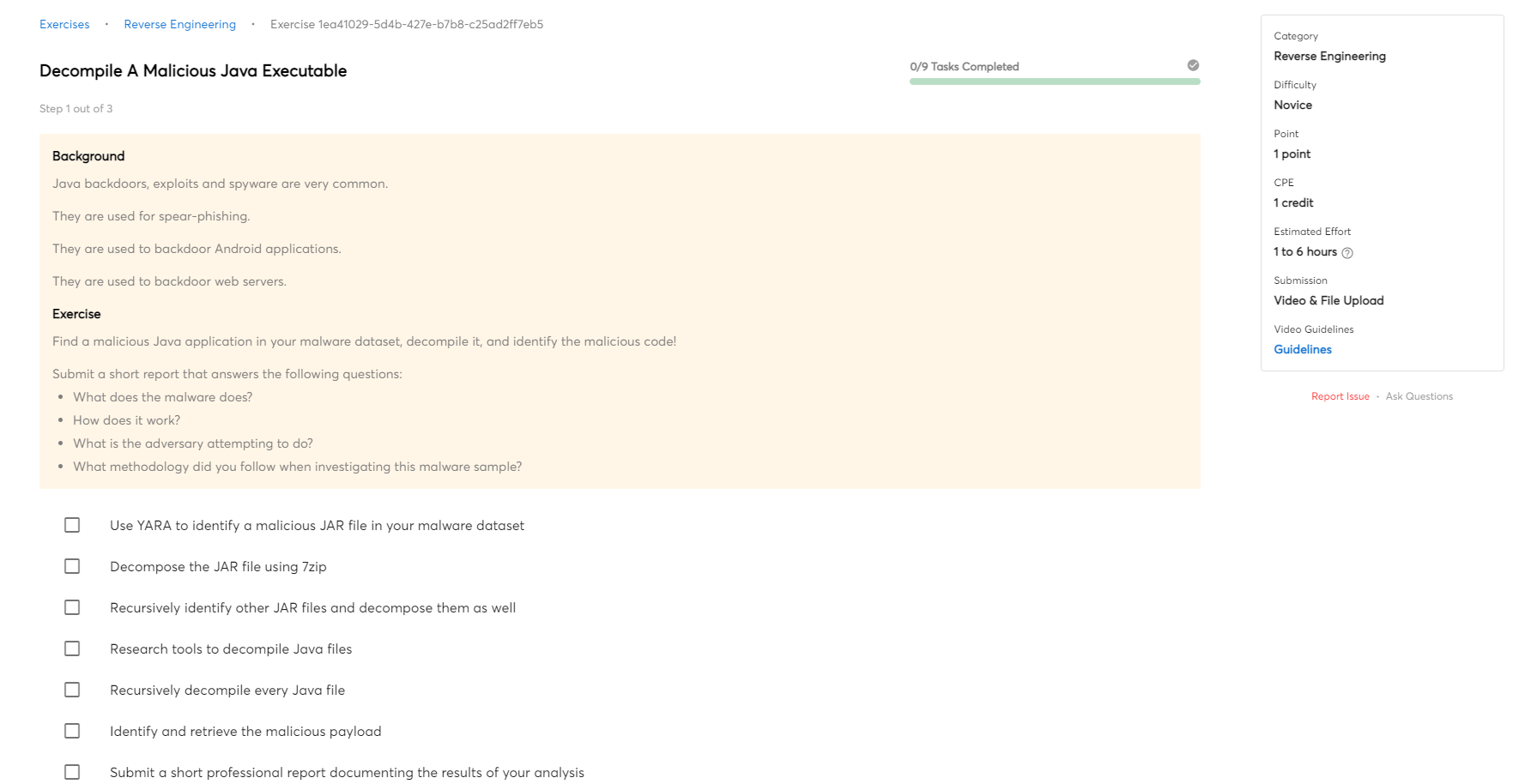
Defeat The Software Breakpoint Detection Anti-Debugging Technique (Advanced Beginner)
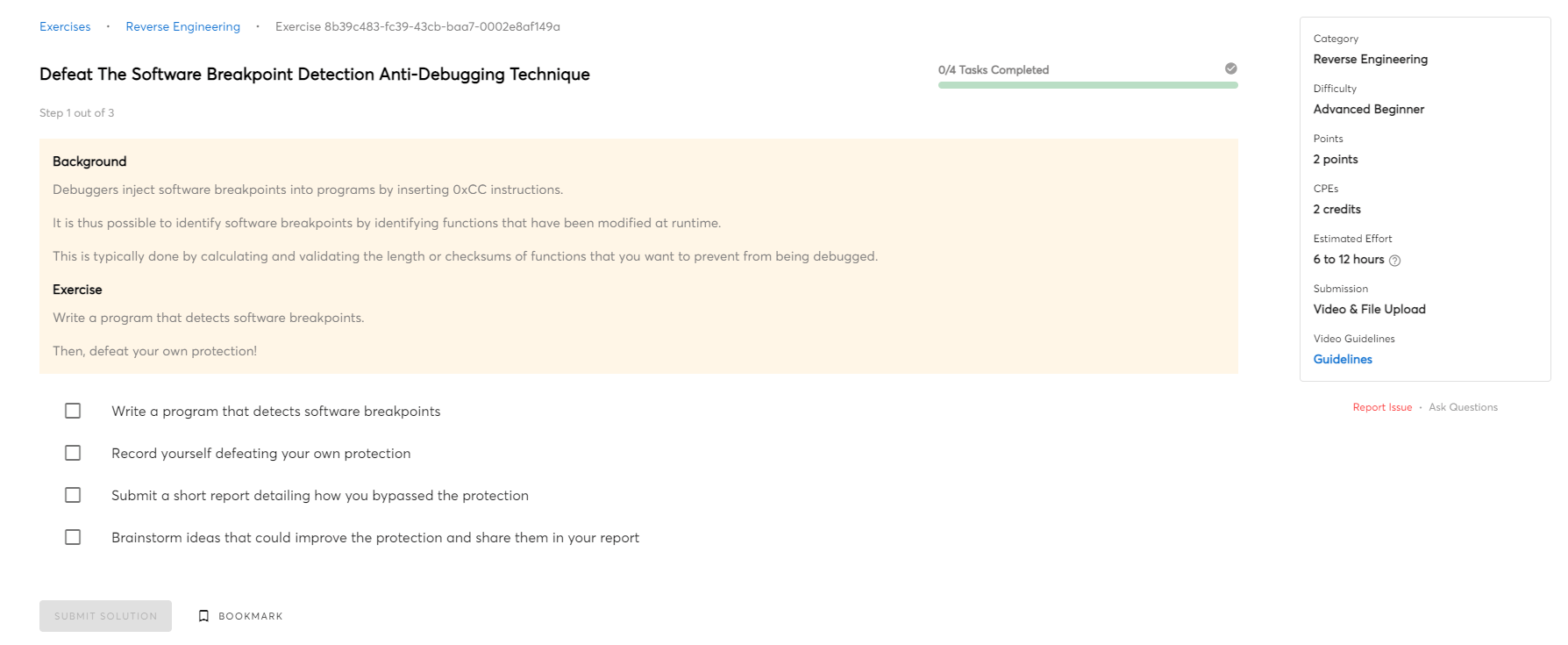
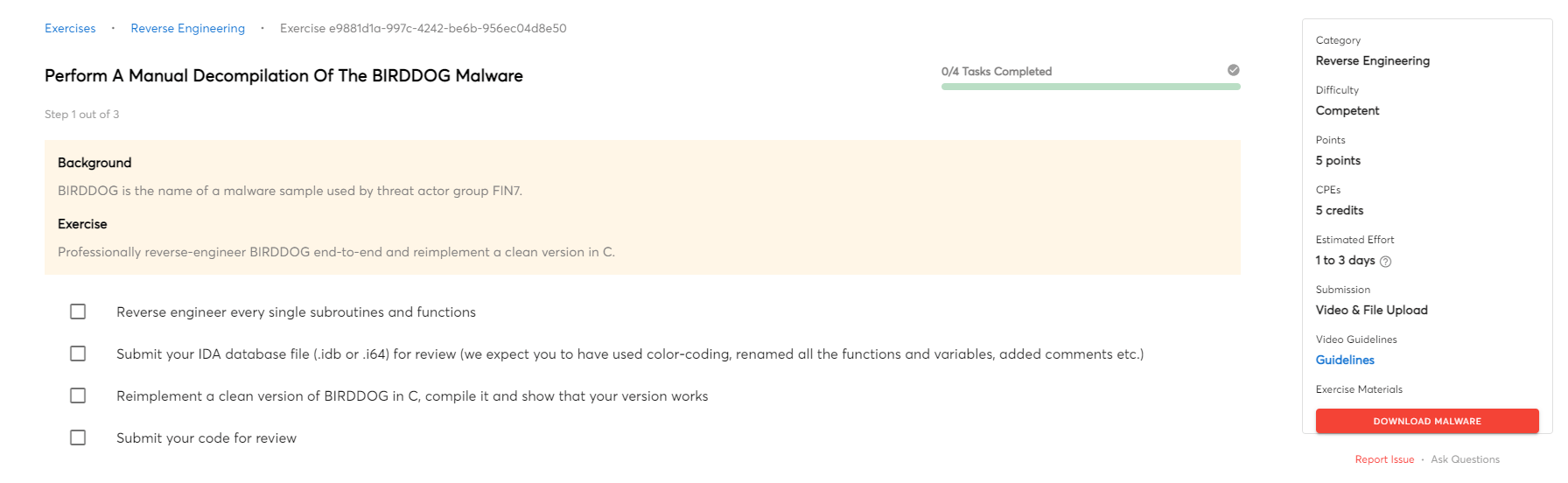
Perform A Manual Decompilation Of The BIRDDOG Malware (Competent)
Help and Support
Unmatched Mentorship: Accelerate Your Growth
At MCSI, mentorship is built to unlock your full potential. Receive personalized insights from multiple experts, tackle real-world challenges, and get the guidance you need to grow rapidly and excel in your cybersecurity career.
-
Personalized feedback with an average instructor response time of 1 business day
-
Direct access to instructors and peers via a 24/7 Discord server
-
Progress tracking and milestone assessments to keep you on course toward success
-
95% of MCSI graduates land cybersecurity jobs with expert mentoring and feedback
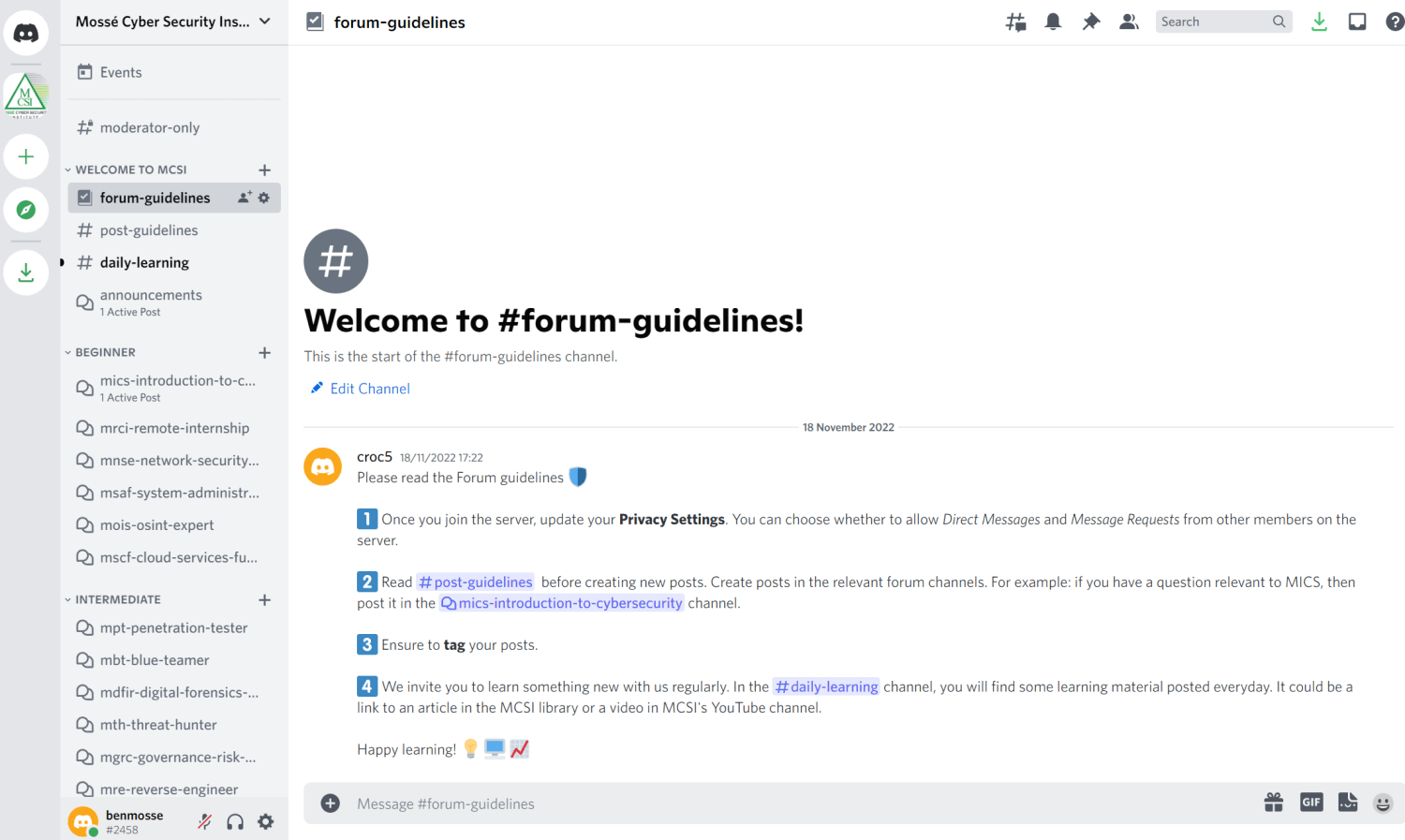
24/7/365 Discord Community:
If you're looking for additional support during your studies, consider joining our Discord server. Our community of fellow students and instructors is always available to provide help and answer any questions you may have.
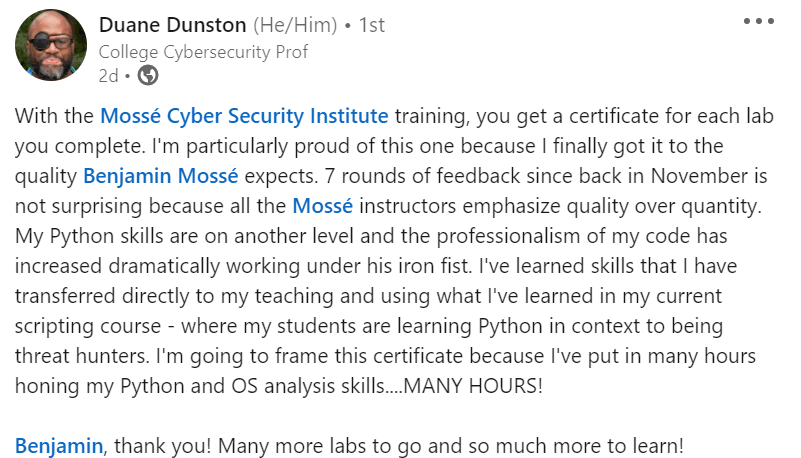
Personalized Support:
Your submissions will be reviewed by MCSI instructors, who will provide you with personalized feedback. This input is critical since it can assist you in identifying the areas where you need to enhance your skills. The instructor's feedback will also tell you how well you did an exercise and what you can do to improve your performance even further.
Click here to see an example of personalized feedback.
Our personalized support will take your skills to the next level. Read what a student says about it:
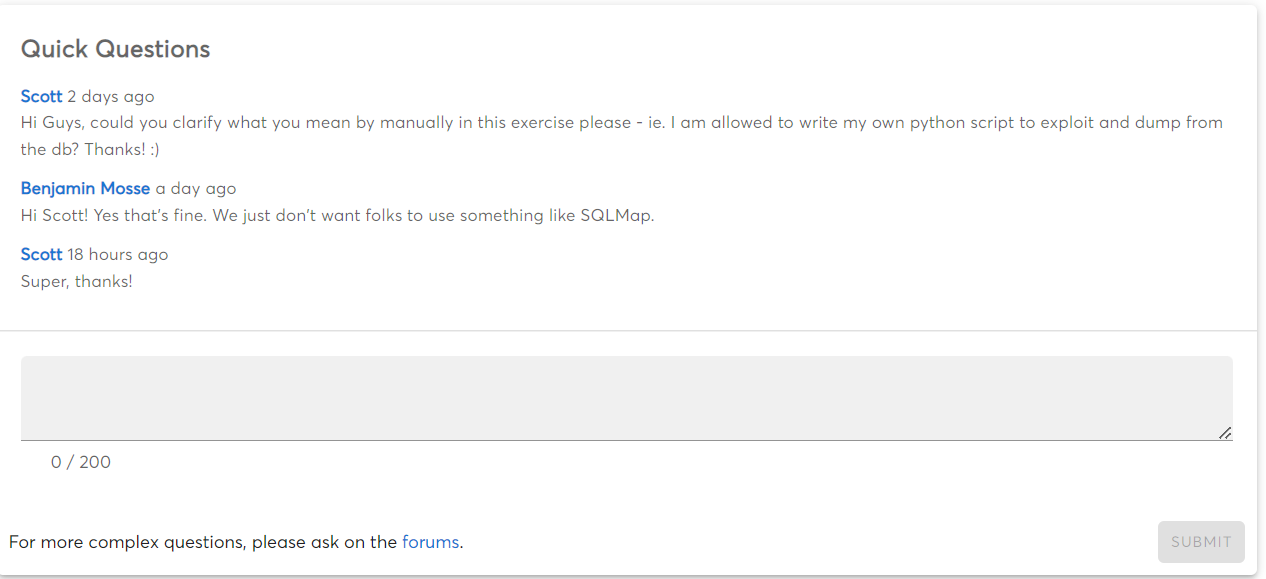
Quick Questions:
If you have any questions or need clarification on any of the exercises, MCSI offers a Quick Questions section on each exercise where you can ask for help. This is a great resource to use if you need assistance. This feature is only available for paid courses.
Prerequisites
Training Laptop Requirement
This course can be completed on a standard training laptop. To ensure you have the necessary hardware to complete the course, your machine should meet the following specifications:
-
64-bit Intel i5/i7 2.0+ GHz processor or equivalent
-
8GB of RAM
-
Ability to run at least (1) virtual machine using Virtual Box, or an equivalent virtualization software
-
Windows 10 or later, macOS 10 or later, or Linux
-
Local administrator privileges
Do you support older operating systems?
Yes. Many of the exercises can be completed on older OS versions. A few of our students are successfully using older equipment to learn cyber security.
Proficiency in the English language
You must have the ability to comfortably read and understand IT documentation written in English. Ideally, they have an IELTS score of 6.5 with no band less than 6 (or equivalent).
Note: You can register for this course without having undertaken an English test.
Programming Skills
We recommend that you have some experience in software programming prior to registering for this course. The preferred programming languages for this course include: Assembly, Python and C.
Lab Environment
This course teaches you how to setup and configure your own cybersecurity lab.
-
Save thousands by avoiding the costs of pre-built labs
-
Customize your lab with the hardware and software you prefer
-
Gain practical skills in networking, system administration, and technical troubleshooting
-
Build confidence by practicing tasks you'll need to perform in real-world jobs
-
Manage and maintain your own tools—just as employers expect in the workplace
Aptitude Test (Optional)
This is an intermediate course. It includes exercises for novices but assumes that they have competent IT skills and a strong understanding of cybersecurity concepts.
Aptitude Test:
If you're not sure if you'll be able to fully enjoy this course, then contact us via email to organize a free aptitude test. This test will determine whether you meet the course's basic baseline criteria. If you've never studied with us before, it will also introduce you to the MCSI Method™.
Easier Courses:
If you are convinced that this course is too difficult for you, then you should start with something easier. We recommend checking out the following courses:
You won't need to complete all of these easier courses in their entirety. Most likely, you already have adequate skills and only need to fine-tune them before taking an intermediate course like this one. Choose a route, follow it, enhance your skills, and then return to this course in a few months!
Free Study Materials
We place a major emphasis on teaching practical skills. Our students learn best when they can put what they've learned into practice. In addition, we believe that many significant thoughts and ideas should be publicly accessible to anyone. We believe that knowledge that is already available in the public domain should not be subject to price.
Purchasing a course is a significant investment. It's critical to know what the course entails and what you intend to get out of it. If you're on the fence about whether or not to buy this course, you might want to check out our library for more information. Concepts, terminology, and essential principles are all taught in our library. This will give you more details about the topics that will be addressed in the course.
🔥
Click here to read more articles from our online library.

 Intermediate
Intermediate