Got a compromised system? Don’t Panic. Investigate.
The first move in incident response isn’t action - it’s understanding.
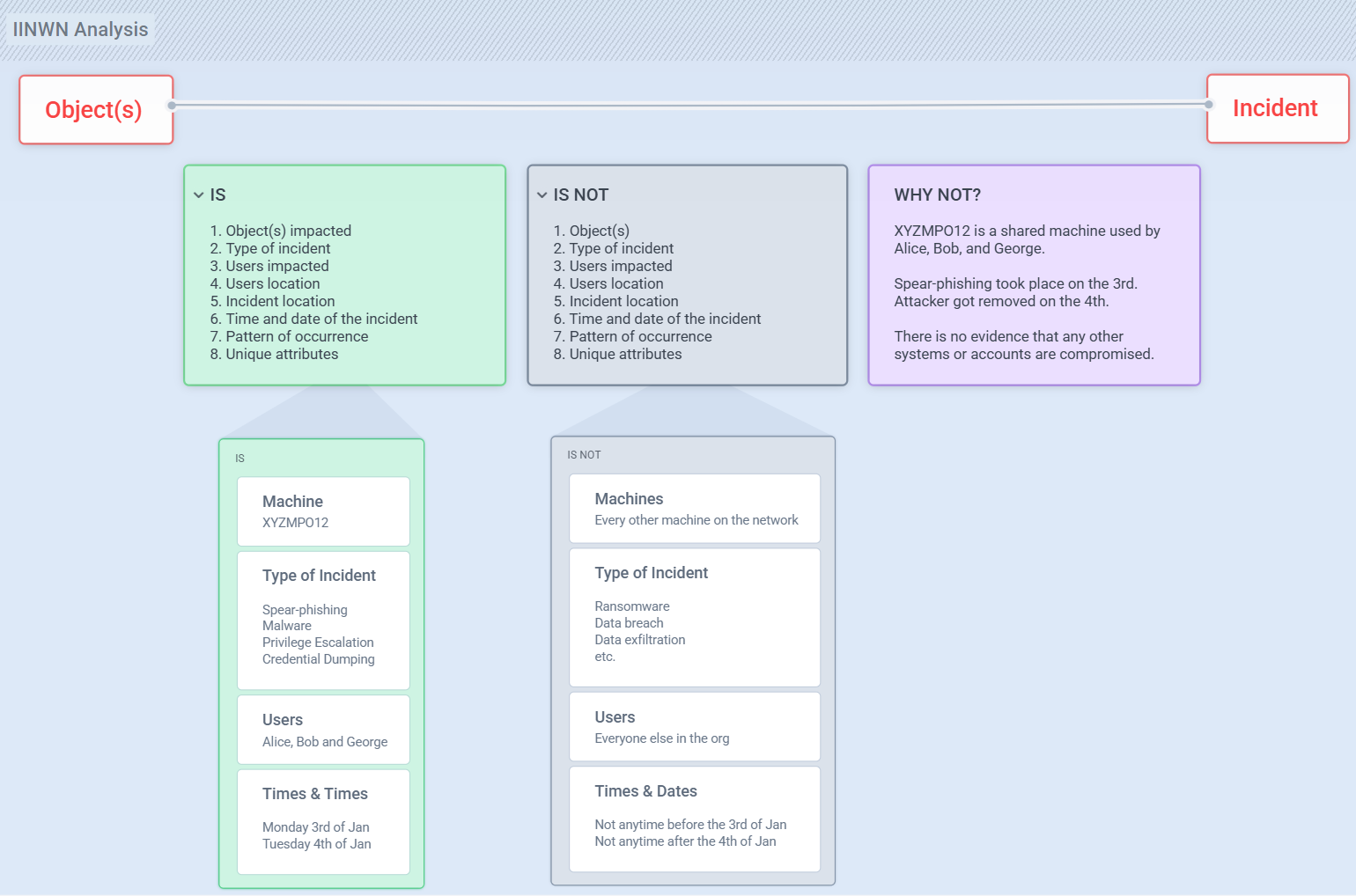
I use a simple framework that’s helped me resolve over 100 cyber incidents with clarity and speed. It’s called:
“Is? Is Not? Why Not?” (IINWN)
Here’s how it works:
| Create a table with 4 columns: **Dimension | Is | Is Not | Why Not** |
Then work through the dimensions that matter in every incident:
Object(s) impacted
Type of incident
Users impacted
User locations
Incident location
Time and date
Pattern of occurrence
Unique attributes
Now fill in only what you know for certain. No assumptions. No guesses.
Everything you don’t know becomes your marching orders for digital forensics. That’s your gap list.
Keep going until every “Why Not” has evidence behind it—logs, memory captures, host-based artifacts.
When done right, you’ll not only understand what happened—you’ll eliminate uncertainty.
And that’s how you respond with precision, speed, contain the incident, and recover with confidence.
