Restricting admin privileges is one of the most common recommendations in cybersecurity. And like most good advice, it’s easier said than done.
The truth is, every system needs someone or something with privileges.
Database admins need access to databases.
Customer support needs to see customer records to respond to queries.
A legal team needs admin rights to manage case files in their case management system.
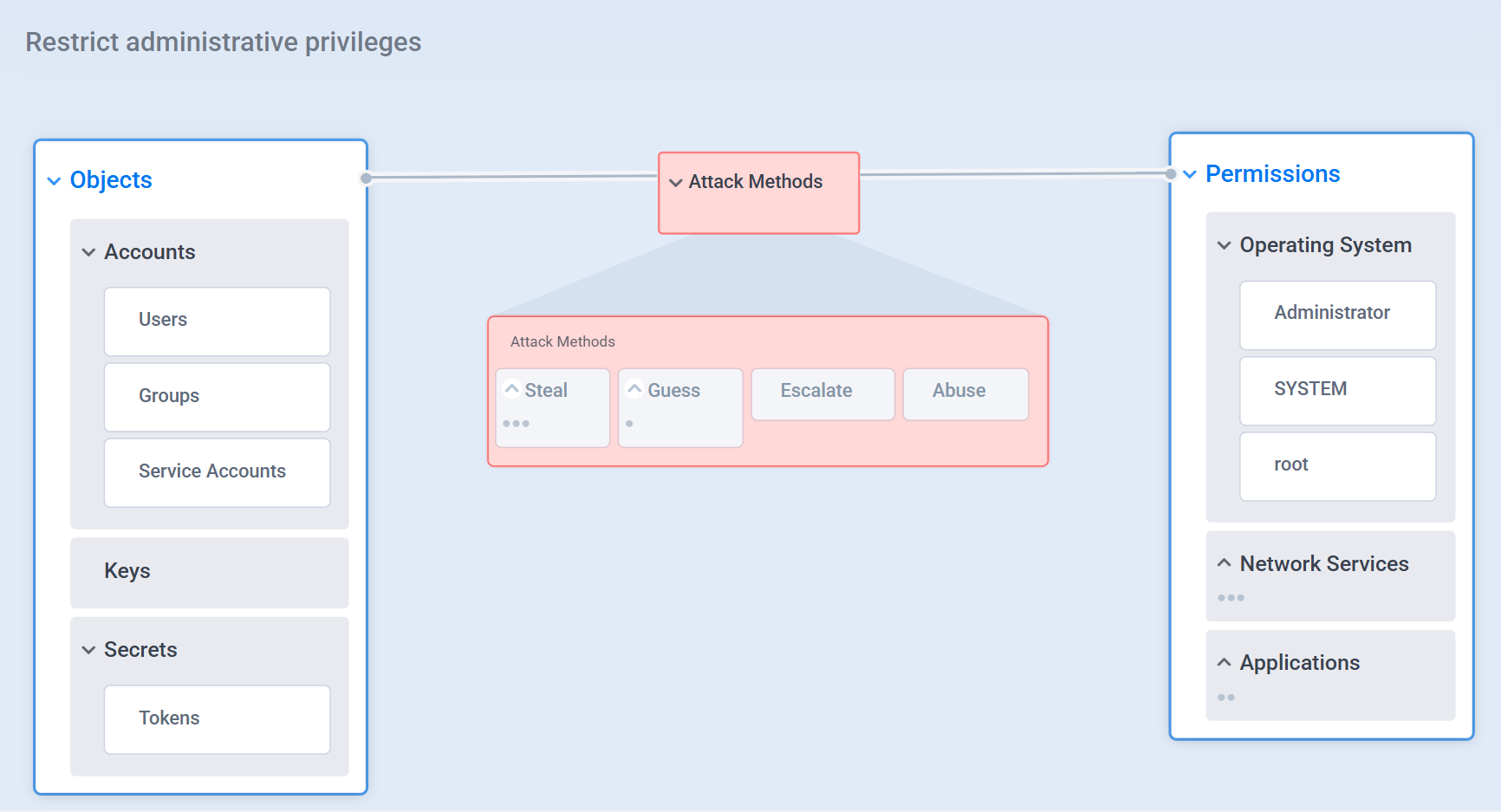
The real challenge isn’t knowing that privileges should be limited.
The challenge is understanding where they exist across your environment and how they’re being used.
Too often, the guidance focuses narrowly on Windows domain accounts. Reduce domain admins.
Use bastion hosts. Those are smart steps if your goal is stopping ransomware.
But if your goal is broader - as it should be - you need to go deeper.
Start by auditing your critical applications, network services, and every type of credential or privileged account.
Only then can you begin to build the right controls around them.
