The most dangerous malware doesn’t need to be installed.
It’s already there.
- It’s the file sharing tool rolled out to every employee
- The remote access utility your IT team swears by
- The forensics software your security team trusts
- The shortcut file that connects to a sensitive file share
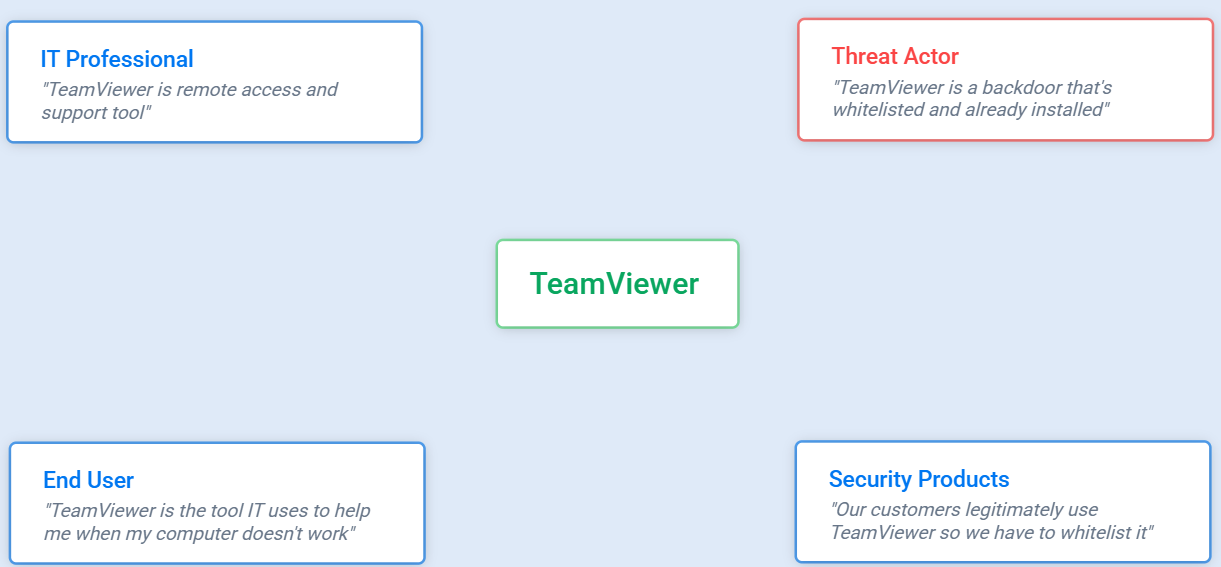
Every time we talk about breaches, we focus on flashy techniques, new vulnerabilities, and headline-grabbing hacks.
But if you talk to penetration testers or Red Teamers, you’ll hear a very different truth:
Give me explorer.exe, and I’ll give you a breach.
The most effective attackers use what’s already trusted, already approved, already embedded in your workflow.
Why? Because the real vulnerabilities are structural.
They’re rooted in how our operating systems were built, how IT is designed to function, and how software is developed under pressure.
The real cybersecurity work begins when we start investigating the layers beneath the headlines, the hype and the trends.
