Yesterday, I was skimming the ACSC Annual Threat Report over lunch.
No surprise - the #1 incident type in Australia is compromised accounts or credentials.
But what struck me wasn’t the finding. It was what was missing.
The report identified the problem and offered some common-sense recommendations. But it didn’t explain which credentials are being compromised. And more importantly, it didn’t explore the deeper web of causes that put those credentials at risk in the first place.
That gap has been gnawing at me. Because this isn’t unique to ACSC. It’s endemic across cybersecurity. We spot the problem, we suggest the obvious solutions, but when they aren’t adopted… we rarely stop to ask why.
So I grabbed a notebook and spent 15 minutes mapping out what the report didn’t say. Within minutes, I had a list:
- Source code with hardcoded credentials never scanned
- Developers who left years ago still able to access repos
- Default builds using reusable credentials
- Cryptographic keys sitting on open file shares
- Legacy apps locked into weak authentication
And that was just the start.
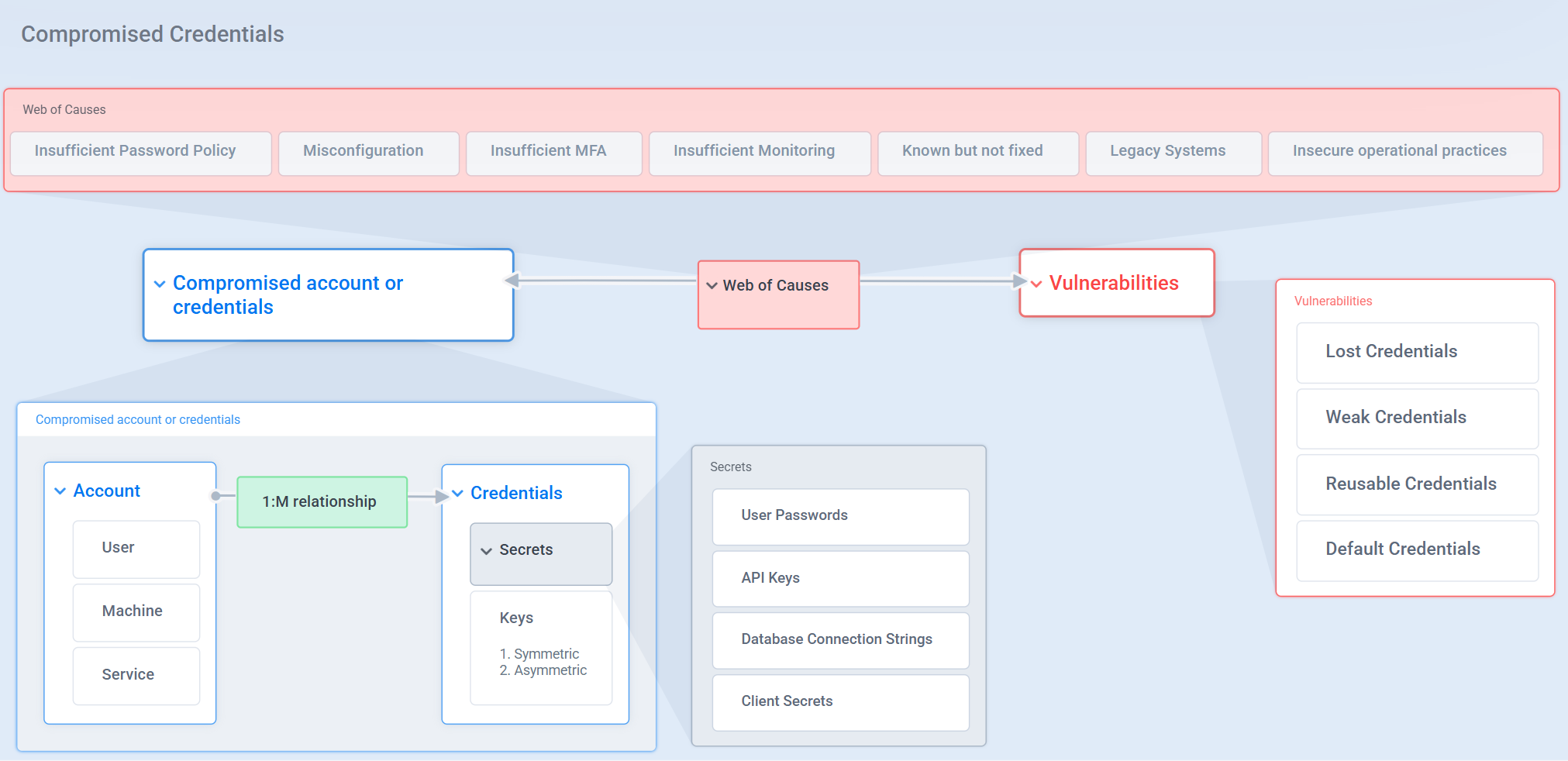
If you’re a CISO - or anyone responsible for defending an environment - you know the first step is understanding all the credential types in play. The second step is harder: unpacking the web of causes that make those credentials vulnerable.
Because here’s the truth: for every cause, you must deploy an anti-cause.
That’s the Great Work!
