Attackers think in Access Loops.
I call the entire process the Always-More-Access Loops (AMAL).
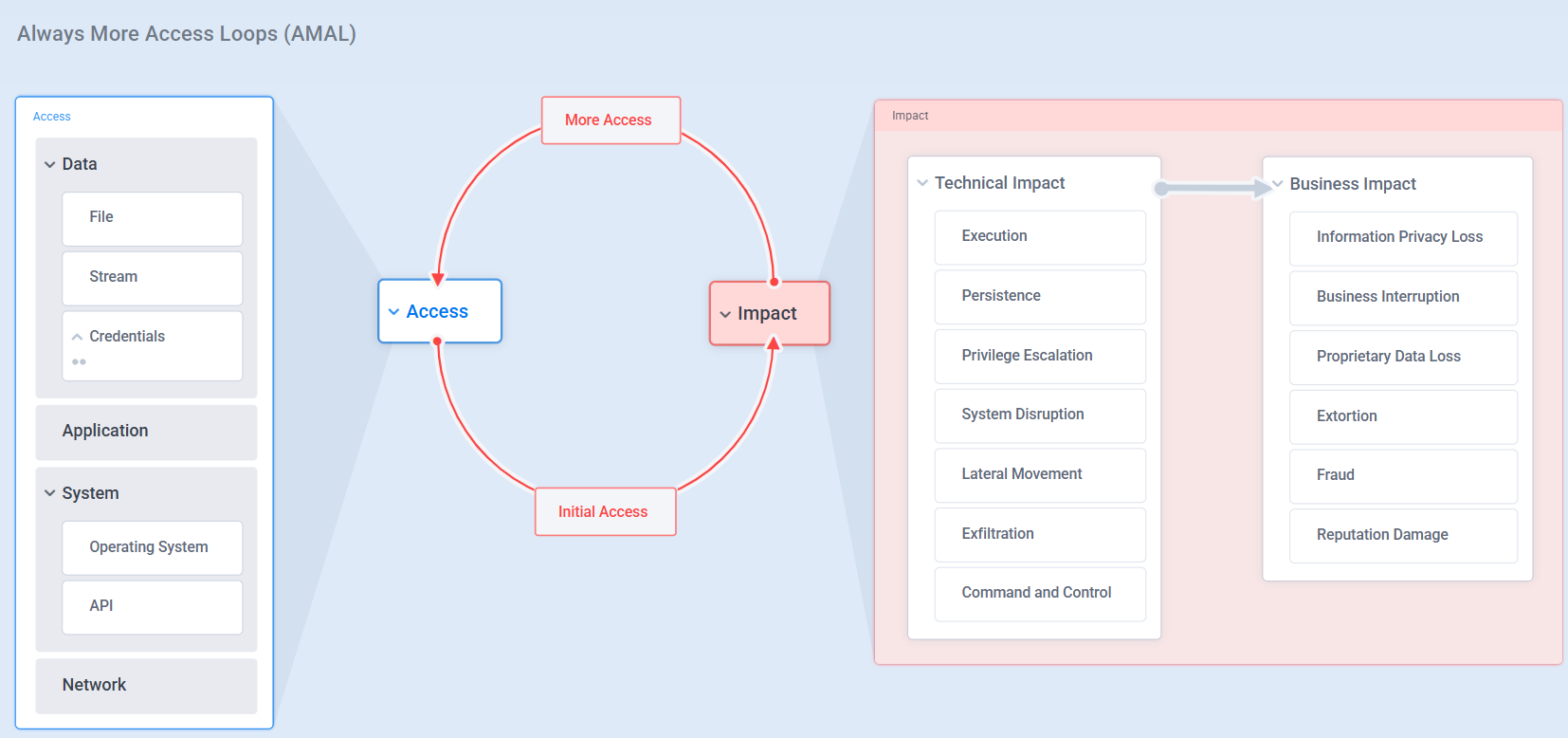
Start with a any type of access (see diagram).
Figure out how to gain more access.
Repeat - until you’ve reached the crown jewels.
It’s how Red Teamers turn “a bug” into “domain admin.” It’s the repetition of persistence, creativity, critical thinking, and problem-solving.
Here’s the opportunity for defenders: think in Anti-Access Loops.
Your goal isn’t just to block the one type or one instance of access by working off a checklist. It’s to prevent the attacker from chaining Access Loops altogether.
A practical starting point:
List all the ways someone could keep expanding access in your environment.
Then, one by one, deploy Anti-Access Loops.
When defenders start thinking in Access Loops, they can anticipate how attackers will behave - and stop them before cyber incidents spiral out of control.
