One of the biggest challenges in cybersecurity is the Shared Infrastructure Problem.
Many of us have experienced it firsthand. It can quietly unravel even the most well-thought-out “Crown Jewels” strategy.
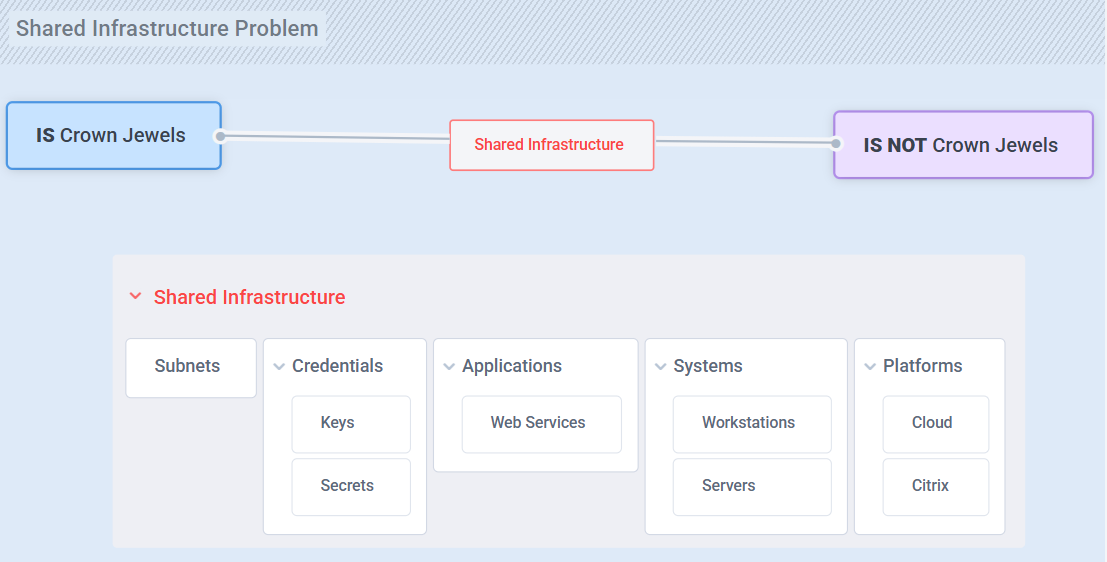
Attackers rarely go straight for what’s most valuable. They start with what’s ignored, under-protected, or shared. A forgotten service account. An internal system that seems low priority. From there, they pivot into the systems that truly matter.
That’s the Shared Infrastructure Problem. It’s not about what’s important to you. It’s about what’s accessible to them.
In my experience, one of the strongest indicators of breach likelihood is how much care an organization puts into protecting what sits outside its Crown Jewels model. Neglect those areas, and it’s only a matter of time before an attacker turns that blind spot into their way in.
