When I started out as a penetration tester, I was regularly finding critical vulnerabilities in almost every application I tested.
Still, I kept hearing the same feedback from peers and mentors:
“You need to translate technical risk into business risk.”
They rarely offered more than that—but eventually, I figured out what they meant.
In cybersecurity, we often describe issues using terms tied to where the asset lives (cloud, SaaS, etc.) and how the attack works (SQL injection, malware).
But that language doesn’t always land with business leaders.
To connect with them, you have to shift the framing:
Use language focused on Threats, Assets, and Effects.
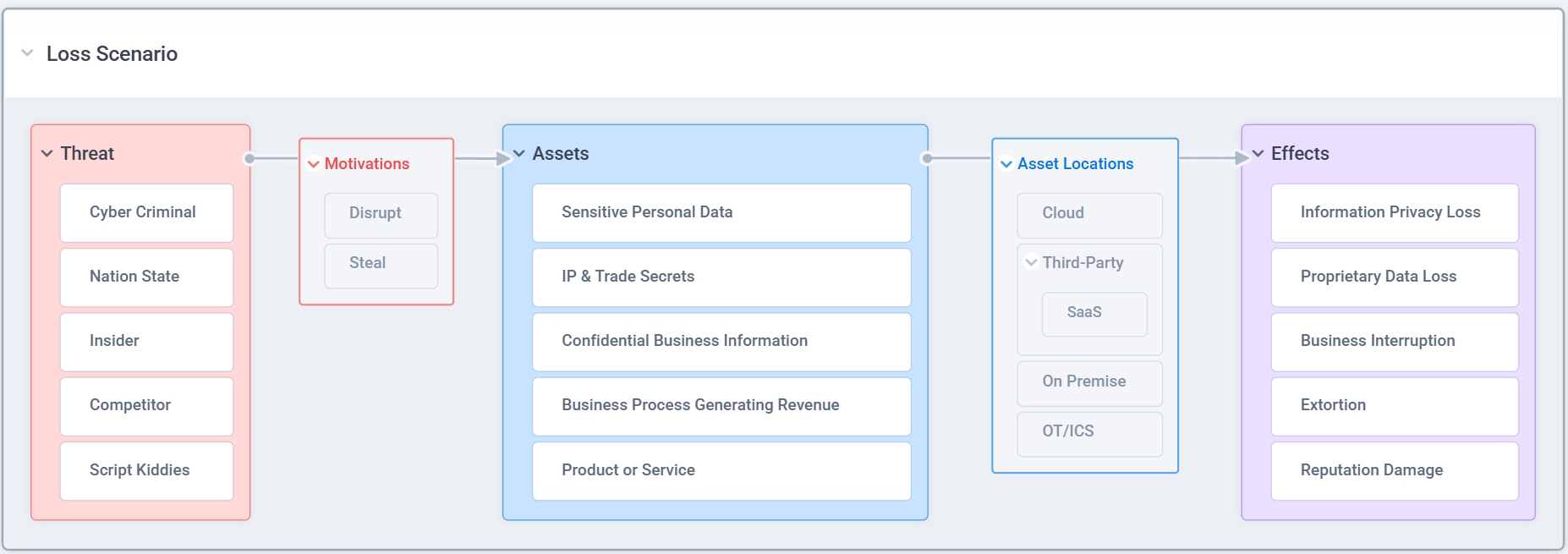
For example:
Instead of saying,
“I could hack your app in AWS and access all your sensitive data using a SQL injection vulnerability.”
Say,
“A financially motivated attacker could gain unauthorized access to sensitive personal information, resulting in an information privacy loss.”
You’re still describing the same risk. But now it’s in terms the business understands - impact, liability, and consequence.
