The ACSC’s 2024–2025 Threat Report urges organizations to implement effective event logging.
If you’re just getting started, break it down into three dimensions:
- Location – cloud, endpoint, OT etc.
- Layer – network, OS, application
- Properties – usefulness and cost
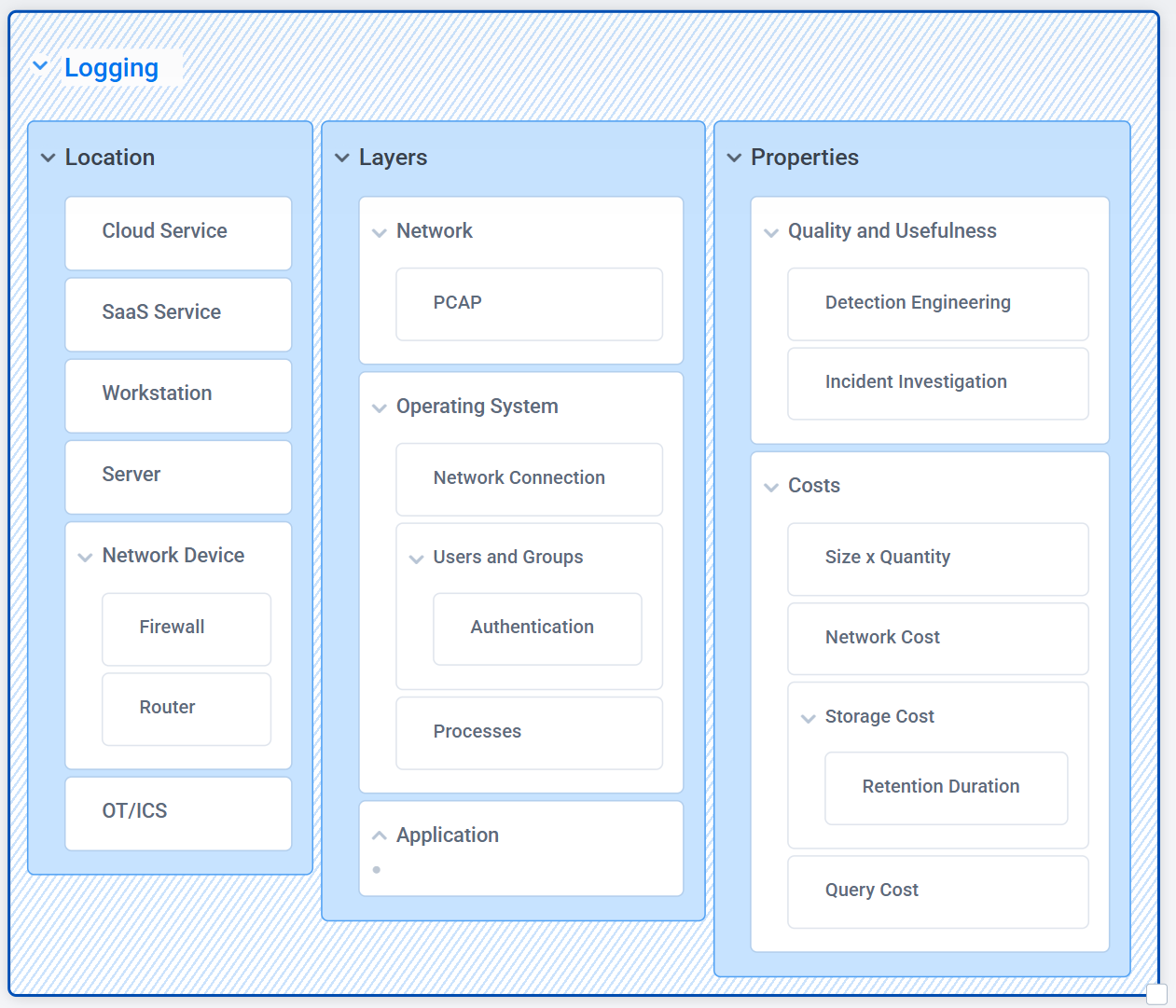
In today’s enterprise, collecting logs is easy. What’s hard - and expensive - is making them useful.
The most under-logged area? Applications.
Why?
Most apps weren’t designed with security logging in mind.
Every app is different, so off-the-shelf detection rules don’t work.
That’s where custom detection engineering comes in.
You’ll need someone who can write tailored rules for your apps and your environment - because generic won’t cut it.
